Botnets have been around since 2004 when the first one was discovered and branded Bagle. The worm was designed to inundate Windows computers with spam, and it was a prototype — an infant form of what botnets would one day become. Your I.T. security team probably wouldn’t see Bagle as much of a threat these days!
Now botnets are capable of infecting a massive number of machines and honing them toward one purpose. Usually, hackers use botnets to inundate network and server connections with traffic; this is what’s known as a DDoS (distributed denial of service) attack, and it can effectively shut down the target website if there are vulnerabilities there. Some servers are capable of flagging suspicious website traffic and kicking off security procedures right then.
Some recent DDoS attacks that you might recall hearing in the news include…
- the 2016 attack on Dyn that shut down Twitter, Netflix, Github, and other huge websites
- when Google services experienced what was, in 2017, the biggest DDoS attack to date
- AWS beat that record in 2020
- the Chaos botnet that affected Windows and Linux devices in September
- when Overwatch 2 gaming servers shut down last month
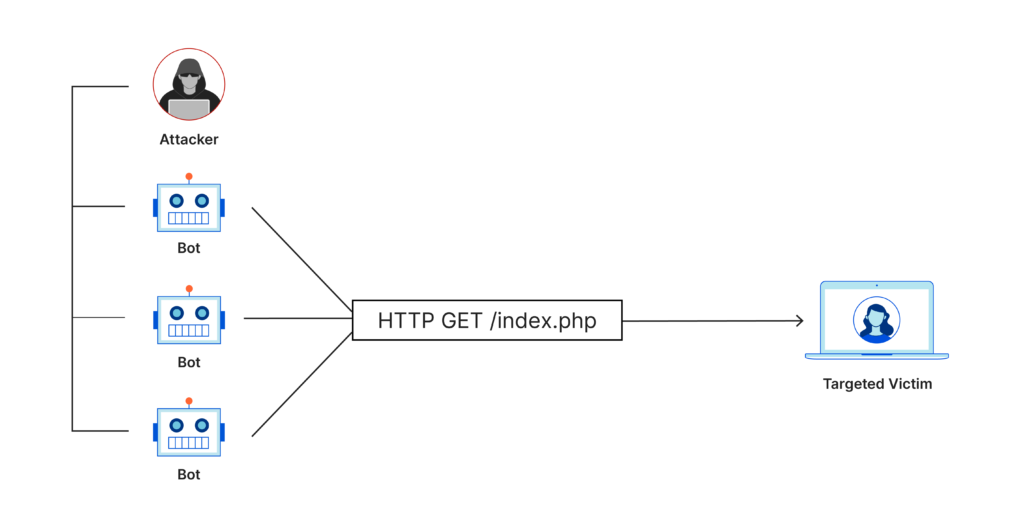
DDoS attacks are getting more dangerous with time, and cybercriminals don’t seem to be shying away from using botnets as a method of breaching your data. With all that in mind, what can you do to keep your network secure from botnet attacks AND your system from becoming a part of the Dark Web’s army?
Table of Contents
What are Botnets?
Botnets are networks of infected devices that are controlled by a central command and control (C&C) server. These networks can consist of thousands or even millions of devices, including computers, servers, mobile phones, and internet of things (IoT) devices. Botnets are typically created by infecting these devices with malware, allowing the attacker to control them remotely.
How do Botnets Work?
Once a device is infected with malware, it becomes a part of the botnet and can be controlled by the attacker. The C&C server sends commands to the infected devices, instructing them to perform specific actions. These actions can include launching distributed denial-of-service (DDoS) attacks, sending spam emails, stealing personal information, and spreading malware.
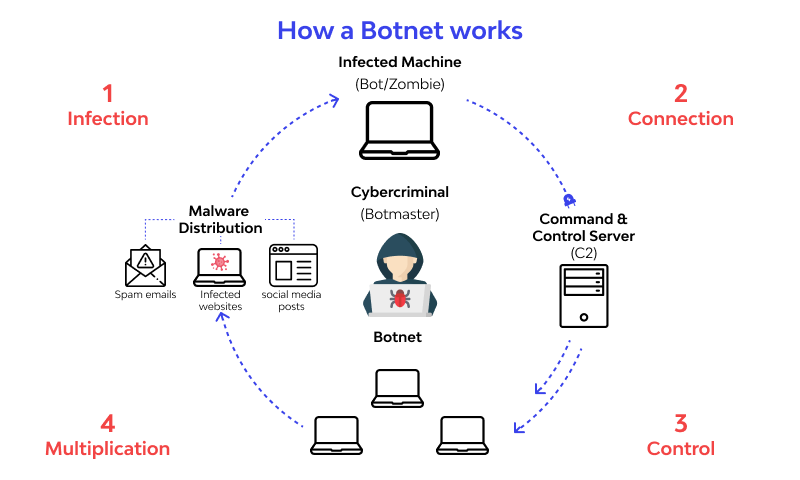
Botnets are often used to launch large-scale attacks, taking down websites and online services. In some cases, botnets have been used to launch attacks on critical infrastructure, such as power grids and transportation systems.
How to Protect Yourself from Botnets
Denial of service attacks is a digital threat that is best monitored via automated scanning software. Artificial intelligence (AI) can self-learn based on inputted information, for example, learning when you usually use the web so they can notify you of unusual activity during the night. If you run a site yourself, you can also use similar services to get insights into your bot traffic and quickly respond to influxes that flag as unusual.
You should also regularly assess your cybersecurity posture to see if there are any known vulnerabilities that botnets might target. NIST-grade Risk Assessments offer insights based on an international database of cyber threats and known exploits. If you turn on regular, automatic updates, then new versions can be downloaded as soon as they’re available, thus protecting you more effectively from zero-day exploits and the latest botnet attacks.
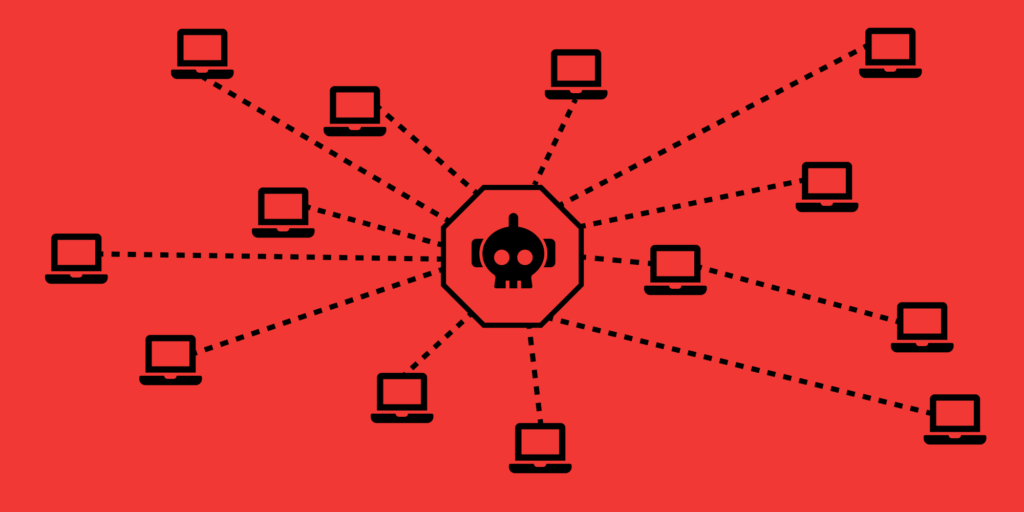
Botnets infect your system with malware the same way that other cyber-attacks start with viruses as the gateway into your network. Avoiding suspicious links, reporting odd messages, and double-checking communications through properly secured channels can all reduce your risk of falling victim to ANY cyberattack, including malware that turns your systems into part of a botnet or starts a DDoS attack on your servers.
Conclusion
Botnet defense is a nearly $300M industry. Cybersecurity experts recognize the threat posed by DDoS attacks and the digital armies that hackers amass to perpetuate their misdeeds. The breadth of today’s threat landscape reflects our rising reliance on the Internet given work-from-home and hybrid work models, increasing digitization the world over, and a general trend toward digital accommodations over physical ones (think how you pay with digital wallets, scan QR codes for restaurant menus and even swipe for dates on an app!) all of which provide hackers more avenues to reach out to us and steal our data.
Knowing what a botnet is, understanding how it enables distributed denial-of-service attacks and equipping your systems with defenses to fight off any attempts to induct them into a botnet, have already given you an advantage. Automated security software can help even more.
Refresh your cybersecurity knowledge, get breaking news, and learn new tricks for staying cyber-secure EVERY DAY by following our blog!
FAQs
What is the purpose of a botnet?
The purpose of a botnet is to allow an attacker to control a large network of infected devices. These networks can be used to launch attacks, steal personal information, and spread malware.
How can I tell if my device is part of a botnet?
It can be difficult to tell if your device is part of a botnet, as the malware used to infect devices is designed to be stealthy. However, if you notice unusual network activity or your device is performing tasks without your permission, it may be a sign that it is infected.
Can antivirus software protect me from botnets?
Antivirus software can help protect you from botnets by detecting and removing malware. However, it is important to keep your antivirus software up to date and to use other security measures, such as strong passwords and two-factor authentication.
References
- https://www.forbes.com/sites/googlecloud/2021/04/01/bot-attacks-are-the-biggest-online-risk-you-havent-addressed/?sh=f3464fc6dda0
- https://www.a10networks.com/blog/the-rise-of-botnet-and-ddos-attacks/
- https://www.marketwatch.com/press-release/botnet-detection-market-2022-statistics-share-price-growth-prospects-industry-trends-till-2028-130-pages-report-2022-10-17
- https://www.zdnet.com/article/hackers-are-using-tech-services-companies-as-a-launchpad-for-attacks-on-customers/
- https://www.msspalert.com/cybersecurity-markets/emea/wip19-threat-group-cyberattacks-target-it-service-providers-telcos

