Malicious files are a common threat to online security, with hackers and cybercriminals using them to infect unsuspecting users with malware. In this article, we’ll explore what malicious files are, how they work, and how you can protect yourself from them.
Entire industries have cropped up to distribute digital files. Remember LimeWire? It was a music pirating software that was shut down for copyright infringement in 2010, disappointing its base of 50M monthly users. That was over a decade ago before the Internet became the widespread phenomenon that it is today. Even then, this number reflected how popular file downloading is and always has been, which is why expert advice to “not download random files” often falls on willfully deaf ears.
The fact of the matter is, it’s convenient and fast to get pictures, Word documents, and anything you want off the web, where people both altruistic and ill-motivated share them widely for free. Today’s blog post will educate you on how to spot the difference between malicious and benign files when you find them out there on the Internet.
Table of Contents
What Are Malicious Files
Malicious files are files that are designed to harm your device by infecting it with malware. Malware is a type of software that can be used to steal personal information, track online activity, or take control of your device.
Malicious files can be disguised as legitimate files, such as PDFs, documents, or images, making them difficult to detect. Once the file is downloaded or opened, malware can be installed on your device without your knowledge.
Types of Malicious Files
- Trojans:
Trojans are malicious files that are designed to look like legitimate files, such as software updates or security patches. Once the Trojan is downloaded and installed, malware can be installed on your device.
- Viruses:
Viruses are malicious files that can replicate themselves and infect other files on your device. Once a virus infects your device, it can be used to steal personal information or take control of your device.
- Ransomware:
Ransomware is a type of malware that can encrypt your files and demand payment in exchange for the decryption key. Ransomware can be spread through malicious files or emails.
Tips to Avoid Malicious Files
Here are 3 tips to stay protected and avoid malicious files:
Avoid EXE Files
In some cases, your job might send you .exe files for a legitimate reason. The file type simply indicates that there is executable code contained within, and it will launch when you open it. Although you might trust your security provider to send you updated software, this presents a clear and avoidable danger when a hacker is the one sending you the files.
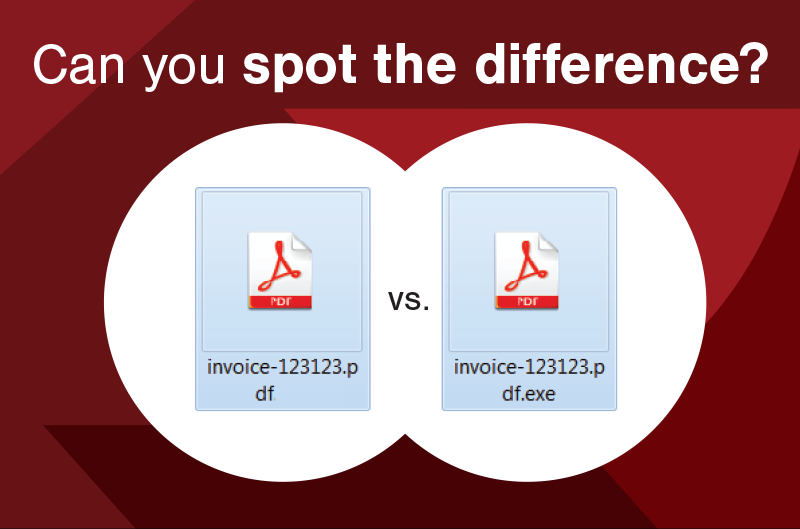
Bad actors may attempt to hide the blatant threat by naming it “Example.pdf.exe” or something similar, hoping you’ll be fooled into overlooking the red flag. Cybercriminals may also reach out to you directly, so beware of random files sent unexpectedly by someone you don’t know. You can also give your antivirus software of choice permission to scan attachments and downloads for malware before allowing it onto the machine at all, cutting off potential threats at the source.
Download Buttons
Sometimes you use a site for the sole purpose of downloading or converting a file there. However, these can be hard to tell apart from real, safe services or even be so cluttered with ads that it’s hard to navigate the legitimate parts of unsecured websites.

Of course, cybersecurity experts recommend avoiding shady sites like this completely, but if you choose to put yourself at risk anyway, then at least remember this trick: Hold the right mouse button over the Download button and drag. If it’s a photo of a Download button meant to trick you into clicking on a malicious website, the image will move with your mouse. If it’s legitimate, the button won’t move.
Web Filters
Whether you’re on a mobile device, laptop, or something else that connects to the Internet, you can add web filtering applications to your line of cyber-defense. They may seem scary because they ask for access to view the online activity and run in the background of all your other apps, but they can be invaluable tools for keeping you safe.
Browser extensions on your preferred computer make it simple. You can also install antivirus apps on your phone that scan new apps, websites, and files to warn you about risky links when you first try to click on them. These tools can check domains, URLs, IP addresses, and more to warn you of any and all suspicious behaviors. They block you from going somewhere unsafe so you have time to navigate back to less murky waters.
Conclusion
There are myriad more complex ways to suss out whether a suspicious file contains malware or not, but these are going to be the simplest and most accessible ways for most users to check the legitimacy of downloadable files they find on the Internet. Automating these scans ensures that you never let a suspicious site slide past. It’s safer than leaving security checks in someone’s hands who may fall victim to human error.
Automated checks run 24/7 to detect threats before they breach your system. Let cybersecurity technologies do what they do best, and keep you protected online.