Businesses rely on technology more and more to manage and retain sensitive data. However, this also makes them vulnerable to many cyber dangers, including phishing attempts, ransomware attacks, and data breaches. A clearly established cybersecurity policy is essential to reducing these risks.
Table of Contents
Understanding the Threat Landscape
Understanding the dynamic threat landscape is crucial when developing a cybersecurity policy. Keep up with the most recent online dangers, including malware, social engineering assaults, and zero-day vulnerabilities. You may successfully adjust your cybersecurity measures by being aware of these dangers.
Assessing Your Business’s Vulnerabilities
Conduct a thorough analysis of the vulnerabilities in your company. Determine any potential weak areas in your infrastructure, including out-of-date software, passwords that are easy to guess, and inadequate network security. This evaluation will serve as a starting point for creating your cybersecurity policy.
Developing a Cybersecurity Policy Framework
Establish a strong cybersecurity policy framework that supports your company’s goals and conforms with all applicable laws. Establish defined objectives, roles, and duties for each individual involved in protecting the data and systems of your company.
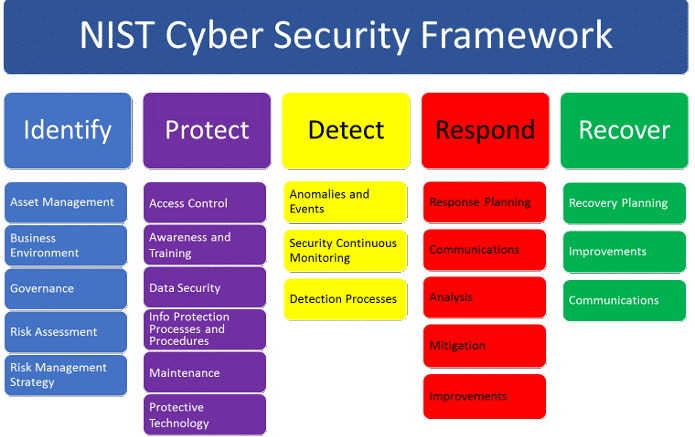
Establishing Access Controls and Authentication Measures
To guarantee that only people with the proper authorizations can access sensitive information, impose strict access controls and authentication procedures. To reduce the danger of illegal access, use strong passwords, multi-factor authentication, and role-based access controls.
Implementing Regular Software Updates and Patches
Update and patch all software and programs used by your company on a regular basis. Cybercriminals can frequently exploit flaws in outdated software. Maintaining updated systems lowers the possibility of successful attacks.
Educating Employees about Cybersecurity Best Practices
In order to foster a culture of security awareness within your company, teach your employees the best practices for cybersecurity. Inform them on how to spot phishing emails, create secure passwords, and report any questionable activity. To maintain a high level of security awareness, regularly reinforce these procedures.
Monitoring and Detecting Potential Breaches
Install reliable monitoring solutions to find any potential network breaches or shady activity. To proactively identify threats, use SIEM (security information and event management) solutions, log analysis tools, and intrusion detection and prevention systems.
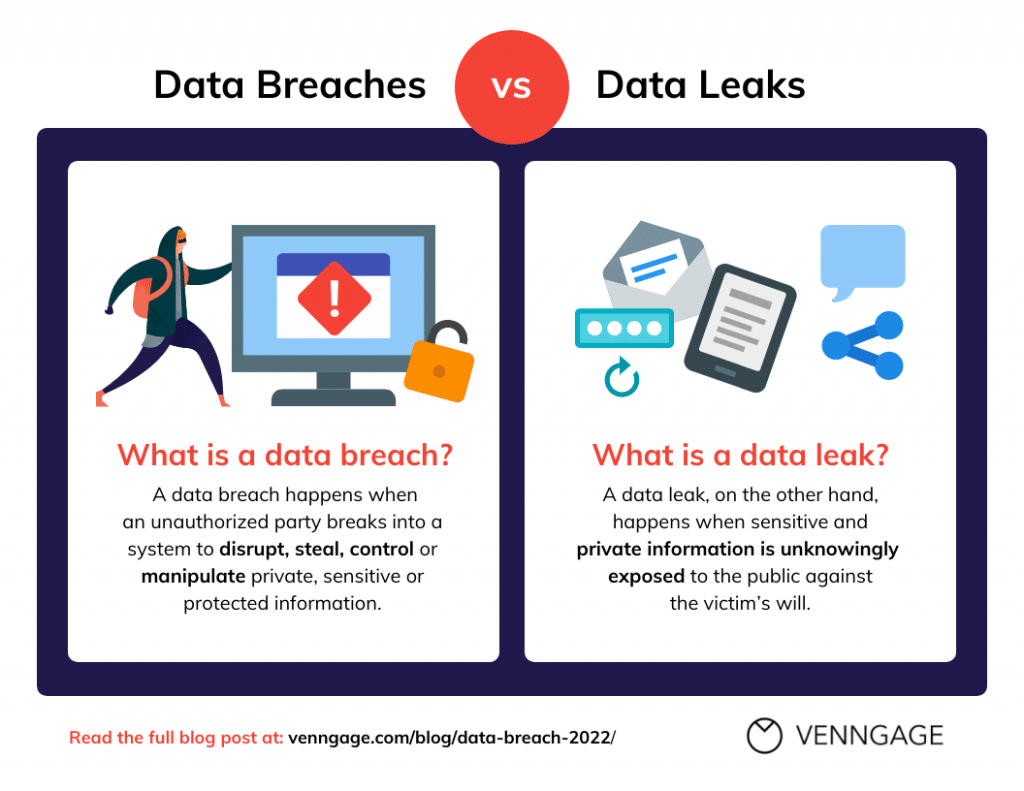
Responding to Cybersecurity Incidents
Create an incident response plan with clear procedures for what to do in the event of a cybersecurity problem. This plan should outline how to stop the breach, lessen its effects, alert the necessary parties, and start the recovery process. To make sure this strategy is effective, test and update it frequently.
Conducting Regular Security Audits
To assess the success of your cybersecurity efforts, conduct routine security audits. Determine any holes or weak points in your infrastructure, and make immediate repairs. Audits support proactive behavior and continual practice improvement in cybersecurity.
Collaborating with External Security Experts
To improve your organization’s security posture, think about collaborating with outside cybersecurity professionals. These professionals can offer insightful analysis, carry out penetration tests, and make suggestions to improve your cybersecurity architecture.
Evaluating and Improving the Cybersecurity Policy
Continually assess the performance of your cybersecurity policy and make any necessary alterations in light of new threats and industry best practices. To remain ahead of potential hazards and guarantee the continuous security of your company, always improve your policies.
Conclusion
You must implement a robust cybersecurity policy if you want to protect your company from emerging cyber threats. You may safeguard sensitive information, uphold client confidence, and ensure the continuity of your business operations by comprehending the threat landscape, analyzing vulnerabilities, and putting strong security measures in place. Contact T3 Today to get started!

