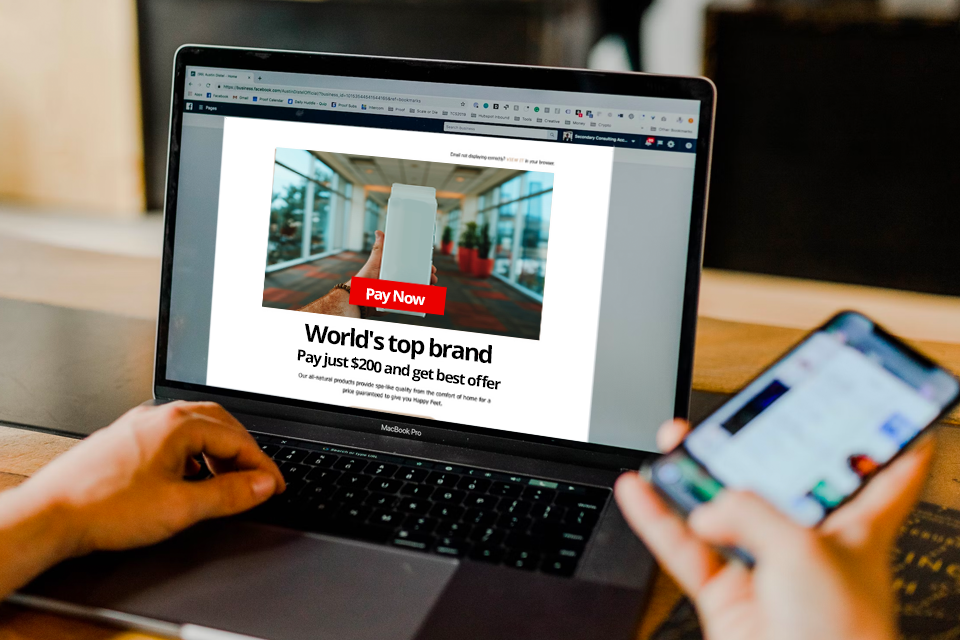
Botnets: Are YOU Part of this Painful Digital Threat?
Botnets have been around since 2004 when the first one was discovered and branded Bagle. The worm was designed to inundate Windows computers with spam, and it was a prototype — an infant form of what botnets would one day become. Your I.T. security team probably wouldn’t see Bagle as much of a threat these … Read more