Imagine waking up one day only to find that all your precious files and data on your computer have been encrypted and held hostage. This nightmare scenario has become a grim reality for countless individuals and organizations affected by ransomware attacks. Ransomware is a form of malicious software designed to encrypt files on a victim’s computer or network, rendering them inaccessible until a ransom is paid to the attackers.
Table of Contents
What is Ransomware?
Ransomware, as the name suggests, is a type of malware that holds your data hostage for ransom. It is typically delivered to victims through various means, such as malicious email attachments, infected websites, or exploit kits. Once it infiltrates a system, it encrypts files using a complex algorithm, making them unusable without the decryption key held by the attackers. The victims are then extorted to pay the ransom, often in cryptocurrency, in exchange for the decryption key.
How Does It Work?
Understanding the inner workings of ransomware is crucial for comprehending the severity of the threat it poses. Typically follows a systematic process that involves several key steps. Firstly, it gains access to a victim’s system through vulnerabilities or social engineering techniques. Once inside, it encrypts files, leaving behind ransom notes that provide instructions on how to pay the ransom. The decryption key is promised upon successful payment, although there is no guarantee that the attackers will hold up their end of the bargain.
Common Types
Ransomware comes in various forms, each with its unique characteristics and capabilities. Some notable types of it include:
1. CryptoLocker
CryptoLocker is one of the earliest and most notorious ones. It encrypts files on the victim’s system and demands a ransom in exchange for the decryption key.
2. WannaCry
WannaCry caused widespread havoc in 2017, affecting hundreds of thousands of computers worldwide. It exploited a vulnerability in Microsoft Windows systems and spread rapidly across networks.
3. Ryuk
Ryuk is a highly targeted ransomware that focuses on large organizations and demands exorbitant ransoms. It often infiltrates systems through phishing emails or by exploiting vulnerabilities in remote desktop services.
4. Maze
Maze gained infamy for not only encrypting files but also stealing sensitive data. If the victim refused to pay, the attackers threatened to release the stolen data, adding another layer of extortion.
Signs of an Infection
Detecting a ransomware infection early can help mitigate its impact and prevent further damage. Here are some common signs that indicate your system might be compromised:
Encrypted Files and Unusual File Extensions
If your files suddenly become encrypted and have unfamiliar file extensions appended to them, it is a strong indicator of a ransomware attack.
Ransom Notes
Ransomware typically leaves behind ransom notes, either as text files or as wallpapers on the victim’s desktop. These notes provide instructions on how to pay the ransom and regain access to the encrypted files.
Slow System Performance
Ransomware can significantly slow down your system as it encrypts files in the background. If you notice a sudden decrease in performance, it’s worth investigating the possibility of an infection.
Unexpected Network Traffic
Some ransomware strains communicate with their command-and-control servers or other infected systems on the network. Monitoring network traffic can help identify suspicious connections.
Impact of Ransomware Attacks
Ransomware attacks can have severe consequences for individuals, businesses, and even governments. The impact of such attacks goes beyond financial losses. Here are some key implications:
Financial Losses
Ransom payments and the associated costs of recovering from an attack can be financially devastating for individuals and organizations.
Data Loss and Disruption
The encryption of critical files can result in data loss, leading to operational disruptions, reputational damage, and potential legal and regulatory repercussions.
Diminished Productivity and Downtime
Ransomware attacks often cause significant downtime as affected systems are taken offline for investigation, remediation, and recovery.
Loss of Trust
For businesses and organizations, falling victim to an attack can erode customer trust, leading to long-term damage to their reputation and credibility.
Steps to Protect Yourself
Taking proactive measures to safeguard your systems and data is crucial in mitigating the risk of ransomware attacks. Here are some steps you can take:
Keep Software Up to Date
Regularly update your operating system, applications, and antivirus software to patch security vulnerabilities that ransomware could exploit.
Exercise Caution with Email Attachments and Links
Be wary of suspicious emails and refrain from opening attachments or clicking on links from unknown or unverified sources.
Backup Your Data Regularly
Maintain regular backups of your important files and ensure they are stored securely offline or on a separate network.
Use Robust Antivirus and Firewall Solutions
Deploy reputable antivirus software and firewalls to detect and block ransomware before it can infiltrate your system.

Best Practices for Prevention
Prevention is the best defense against ransomware attacks. Implementing these best practices can significantly reduce the likelihood of falling victim to it:
Security Awareness Training
Educate yourself and your employees about the dangers of ransomware, social engineering techniques, and safe online practices.
Implement Multifactor Authentication
Enable multifactor authentication (MFA) wherever possible to add an extra layer of security to your accounts and systems.
Restrict User Privileges
Limit user privileges to the minimum necessary for their job function to reduce the potential impact of an infection.
Network Segmentation
Segment your network to isolate critical systems and sensitive data, making it harder for ransomware to spread across your network.
What to Do If You’re a Victim
Despite the best preventive measures, ransomware attacks can still occur. If you find yourself in this unfortunate situation, here’s what you should do:
Isolate Infected Systems
Immediately disconnect the infected systems from the network to prevent further spread of the ransomware.
Report the Incident
Contact your IT department or a trusted cybersecurity professional to report the incident and seek assistance in handling the situation.
Preserve Evidence
Document all relevant information about the attack, including ransom notes, communication with attackers, and any other details that may aid in the investigation.
Do Not Pay the Ransom
Law enforcement agencies and cybersecurity experts strongly advise against paying the ransom, as it fuels further criminal activities and does not guarantee the recovery of files.
Data Backups
Regularly backing up your data is one of the most effective strategies to combat ransomware. Here’s why data backups are crucial:
Data Recovery
Having up-to-date backups allows you to restore your files without paying the ransom, minimizing the impact of a ransomware attack.
Test Your Backups
Regularly test your backups to ensure their integrity and reliability. A backup is only valuable if it can be successfully restored when needed.

The Role of Cybersecurity in Combating It
Cybersecurity professionals and organizations play a vital role in defending against ransomware. Here’s how they contribute to the fight against this menace:
Threat Intelligence and Analysis
Cybersecurity experts continuously monitor and analyze threats, sharing their findings to help organizations enhance their defenses.
Incident Response and Recovery
In the aftermath of a ransomware attack, cybersecurity teams provide swift incident response and support in recovering affected systems and data.
Vulnerability Management
Identifying and patching vulnerabilities in software and systems is a critical task performed by cybersecurity professionals to prevent attacks.
Ransomware in the Modern World
Ransomware has evolved significantly over the years, adapting to new technologies and exploiting vulnerabilities in our increasingly interconnected world. Here are some key aspects:
Targeting Critical Infrastructure
Recent years have seen an increase in ransomware attacks targeting critical infrastructure, such as hospitals, utilities, and transportation systems, with potentially life-threatening consequences.
RaaS
Ransomware as a Service (RaSS) has emerged as a lucrative business model, allowing even novice cybercriminals to launch attacks with minimal technical expertise.
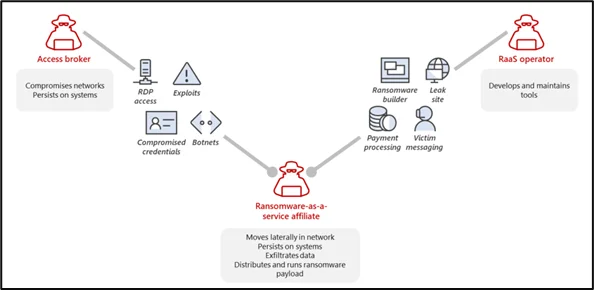
Double Extortion Tactics
Many ransomware groups now engage in double extortion, threatening to leak stolen data if the victim refuses to pay the ransom, amplifying the pressure on organizations to comply.
What Lies Ahead in The Future
As technology advances, so does the threat landscape. The future of ransomware holds both challenges and opportunities in the ongoing battle against cybercriminals:
AI-Powered
Cybercriminals are likely to exploit artificial intelligence (AI) and machine learning (ML) techniques to create more sophisticated and evasive ransomware strains.
Increased Targeting of IoT Devices
With the proliferation of Internet of Things (IoT) devices, we can expect an increase in ransomware attacks targeting these vulnerable endpoints.
Collaborative Defense Efforts
The fight against ransomware requires collaboration between governments, law enforcement agencies, cybersecurity professionals, and organizations to develop effective countermeasures.
Conclusion
Ransomware continues to be a significant threat in the digital landscape, causing financial losses, data breaches, and disruptions to individuals and organizations alike. By understanding the nature of it, adopting preventive measures, and implementing robust cybersecurity practices, we can fortify our defenses and mitigate the risk of falling victim to these malicious attacks.
Education is prevented! Reading this blog has been a great stride forward in your security awareness. Contact T3 Today to Mitigate any Threats!
FAQs
Can ransomware infect mobile devices?
Yes, ransomware can infect mobile devices, including smartphones and tablets. Mobile users should exercise caution when downloading apps from untrusted sources and regularly update their devices’ operating systems and applications.
Is it possible to decrypt files without paying the ransom?
In some cases, cybersecurity researchers develop decryption tools that can unlock files affected by certain strains of ransomware. However, it is not always possible to decrypt files without the decryption key held by the attackers.
Should I contact law enforcement if I experience an attack?
Yes, it is advisable to report ransomware attacks to law enforcement agencies. They can provide guidance and assist in the investigation, which may help track down the perpetrators.
Are small businesses at risk of attacks?
Yes, small businesses are often targeted by ransomware attackers due to their potentially weaker security infrastructure and limited resources for cybersecurity measures. Small businesses must prioritize cybersecurity and implement preventive measures.
How often should I update my backups?
It is recommended to update your backups regularly, depending on the frequency of changes to your files. Automated backup solutions can streamline this process and ensure your backups are up to date.

