Phishing scams are rampant in today’s cyber environment. Over 90% of data breaches start with a well-placed phishing message. Phishers will set “bait” to draw you into you installing malware or giving them your private information, without having to break in through more time-consuming and convoluted methods.
Cybercriminals are only getting smarter with their manipulation, too. New terminology has been invented to keep up with the times:
- Smishing, or SMS phishing, happens over text or DM
- Vishing, or voicemail phishing, are those pesky robocalls you keep getting about your car’s extended warranty or a late bill
- Spear-phishing targets you specifically rather than any account at random
Table of Contents
Most Faked Brand In Phishing
While some scams are easy to spot, others impersonate trusted companies in order to engender trust in the recipient. Hackers will choose big names like Microsoft or Google to increase the likelihood that you have accounts with these ubiquitous services, so therefore it wouldn’t seem out of place to receive a message from them.
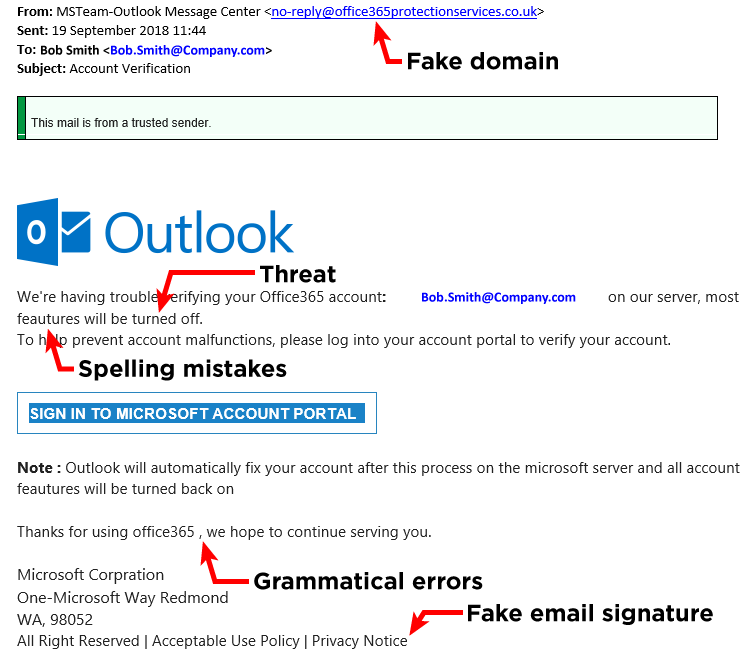
It makes sense that the brand most commonly faked by phishers is LinkedIn, according to the Q2 2022 Brand Phishing Report from Check Point Research. In 2022, phishing scams have impersonated LinkedIn in approximately half of the total attacks.
Maybe you would expect them to go after something like Facebook, but think about it: If the hackers are trying to attack a business, but don’t want you suspicious and/or defended by the more rigorous security protocols at your office, they might target you on a personal but still business-related account. People do a lot of networking, recruiting and so much more on the platform that a good number of working professionals are likely to have an account. If that’s your target demographic as a hacker, then LinkedIn is a sensible disguise.
Protecting Yourself from Phishing
What can you do to avoid falling for the same kind of scam? First, you should know that businesses will never ask you to send your credentials in something as unsecured as an email. They would use a secure server, like their main website, to perform any password changes or payment confirmations, so they couldn’t get intercepted by an unauthorized third party. Click here to learn more about Third-Party Risks.
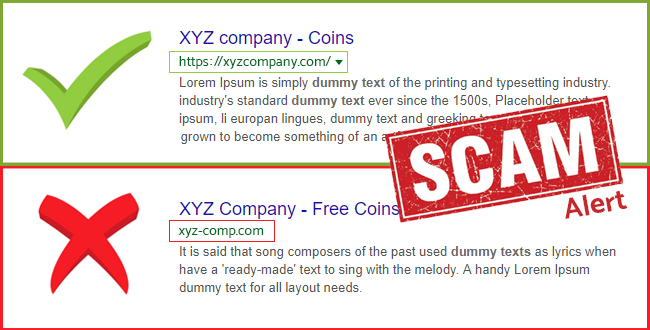
What if the hacker sends you a link to a fake website that they’ve set up to look like the real one? You can always go directly through the main website in a separate tab to ensure that you’re navigating the true site. If you click the link and end up somewhere unsafe, hopefully, your web browser has automated detection services that notify you when you’re trying to navigate somewhere risky. Alternatively, you can recognize fake websites by a few hallmarks:
- No contact information for customer services
- Incorrect or old logos and color schemes
- Misspelled URLs, even by a letter or two; for example, wikiipedia.com or wikipedai.com
- No way to navigate to other parts of the website
- Nothing on the page but a web form to fill out
Conclusion
Be careful with your messages! A spam filter won’t catch every phisher, but that combined with browser protection, firewalls, antivirus software, and a knowledgeable eye for scams can be a huge benefit in your fight to keep your networks hacker-free.
Follow our blog for the latest news updates and tips for staying cyber-secure!